In an era where cyber threats are becoming increasingly sophisticated, safeguarding your business’s sensitive data is no longer a choice, but a necessity. Traditional software-based security measures are often not enough to protect against determined attackers. This is where Hardware Security Modules (HSMs) come in, offering a robust and virtually impenetrable layer of protection for […]
CREAPLUS strengthens its role as a major regional player with new vendors, reselling partners and new employees, contributing to the improvement of the cybersecurity situation in the Western Balkans and the DACH region. CREAPLUS, one of the most important distributors of high-quality and technically sophisticated solutions in the Western Balkan countries, has achieved growth in […]
By understanding phishing tactics and embracing advanced threat monitoring, organizations can disrupt the cycle of phishing attacks, safeguarding both their brand and their customers from the ever-growing threat of cybercrime. Phishing attacks remain a leading cybersecurity threat, increasing by 34% in 2024 compared to the previous year. With 91% of cyberattacks starting from phishing emails, […]
Hardware Security Modules (HSMs) emerge as critical components of a robust security infrastructure, acting as impenetrable fortresses for your most valuable cryptographic keys and sensitive data. In an era defined by digital transformation and escalating cyber threats, protecting sensitive data is paramount. Traditional security measures, while essential, often prove inadequate against sophisticated attacks. What […]
The cybersecurity landscape is constantly evolving, and 2025 promises to be a year of unprecedented challenges and opportunities for Chief Information Security Officers (CISOs). The rise of artificial intelligence (AI), while offering immense potential, also introduces new threats and complexities. CISOs must stay ahead of the curve by understanding these emerging trends and leveraging AI-powered […]
With the renewal of the ISO/IEC 27001 Certificate of Excellence for Information Security Risk Management, CREAPLUS has confirmed its commitment to security and the continuous improvement of its organization, business processes and customer offer. The market for cyber security solutions and services is constantly evolving, with customers becoming more aware and demanding. CREAPLUS customers face […]
In the face of relentless cyber threats, security testing is not a question of “if” but “how well.” By implementing a comprehensive security testing policy, organizations can proactively defend against attacks, protect their valuable assets, and ensure business continuity. Don’t wait for a cyberattack to expose your vulnerabilities. Proactive security testing is essential to identify […]
According to KuppingerCole, KELA’s intelligence solutions and services enable cyber security teams and organization leaders to take effective actions and decisions to maintain cyber resilience, mitigate business risks and ensure business continuity. KuppingerCole, one of Europe’s leading independent cyber security consultancies, has provided an executive view of KELA’s cyber security intelligence solutions and services. As […]
The Cyber Resilience Act represents a significant shift in the EU’s approach to digital security. It is not just a regulatory requirement, but a strategic investment in the future of secure digital products and services. With cyber-attacks becoming more sophisticated, the need for enhanced security measures to protect our digital lives has never been greater. […]
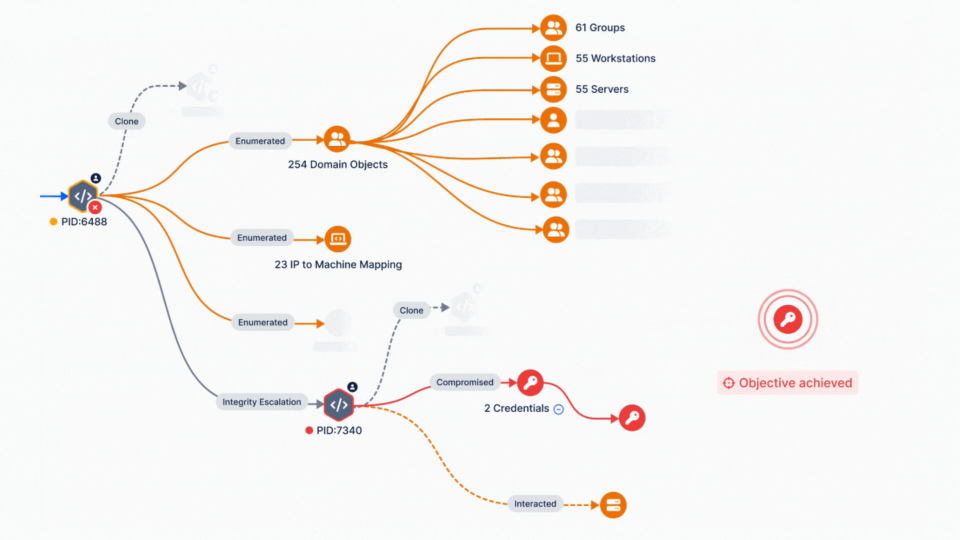
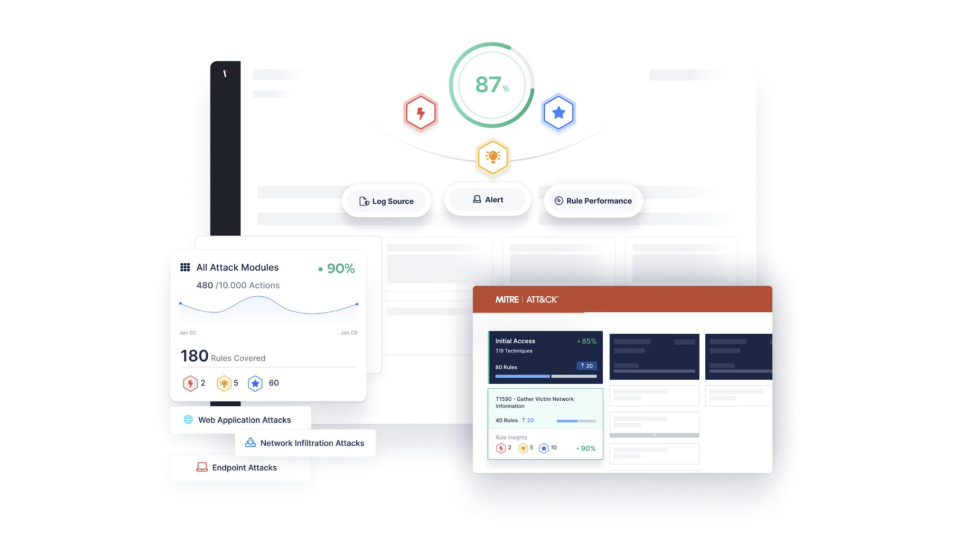
Autonomous pentesting is no longer a luxury—it’s a necessity. Organizations that embrace this technology will gain a significant advantage in protecting their valuable digital assets. The cybersecurity world is at a crossroads. Cyber threats are becoming increasingly complex, but traditional security testing methods are struggling to keep up. They’re often slow, expensive, and can’t cover […]