In the face of relentless cyber threats, security testing is not a question of “if” but “how well.” By implementing a comprehensive security testing policy, organizations can proactively defend against attacks, protect their valuable assets, and ensure business continuity. Don’t wait for a cyberattack to expose your vulnerabilities. Proactive security testing is essential to identify […]
The Cyber Resilience Act represents a significant shift in the EU’s approach to digital security. It is not just a regulatory requirement, but a strategic investment in the future of secure digital products and services. With cyber-attacks becoming more sophisticated, the need for enhanced security measures to protect our digital lives has never been greater. […]
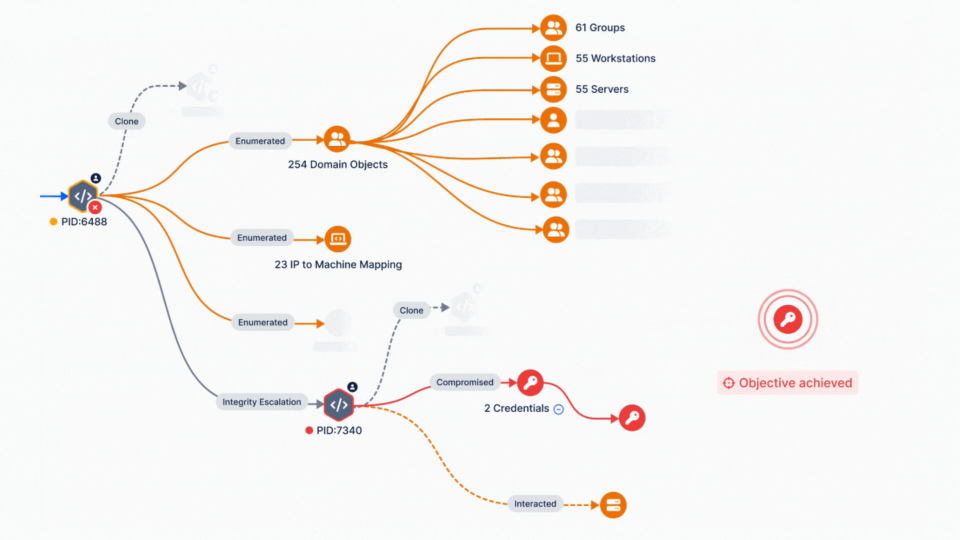
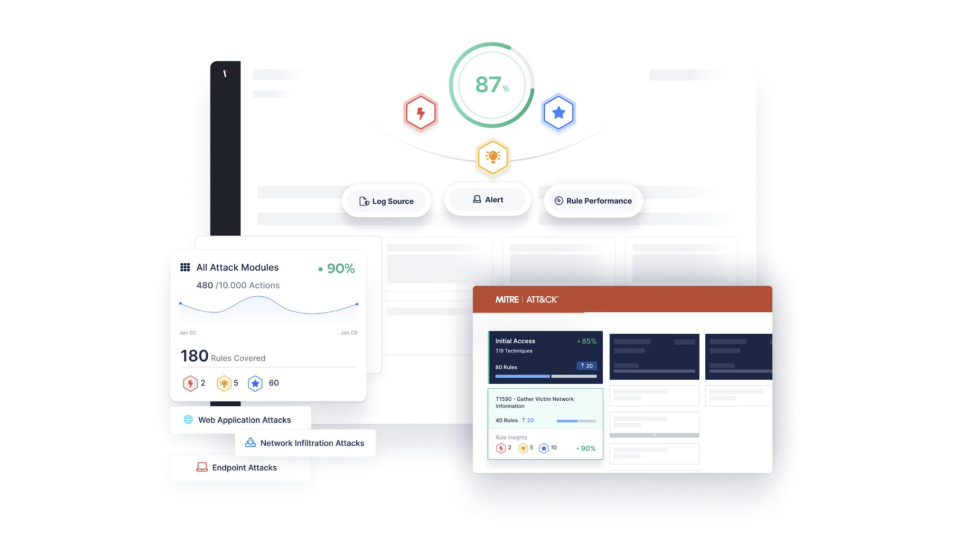
Autonomous pentesting is no longer a luxury—it’s a necessity. Organizations that embrace this technology will gain a significant advantage in protecting their valuable digital assets. The cybersecurity world is at a crossroads. Cyber threats are becoming increasingly complex, but traditional security testing methods are struggling to keep up. They’re often slow, expensive, and can’t cover […]
For decades, public-key cryptography algorithms like RSA and ECC have formed the bedrock of digital security. However, the advent of quantum computing poses a significant threat to these algorithms Quantum computers, with their immense processing power, have the potential to break these cryptographic schemes, rendering current security measures obsolete. This isn’t a distant threat; advancements […]
How to break the blame barrier by building a culture of cybersecurity success. A recent study revealed a worrying trend: 64% of employees hesitate to report security incidents due to fear of repercussions. This blame culture is a ticking time bomb for organizations in our increasingly digital world. Think about it: if your team is […]
Strengthen your SecOps with seamlessly integrated, powerful, AI-driven analytics without having to rip and replace your current infrastructure. Remember the days of clunky SIEM setups that required a dedicated server just to store logs? Thankfully, those days are long gone. Today’s SIEM solutions are all about flexibility and scalability, allowing you to adapt and grow […]
Cyber Threat Intelligence (CTI) can be your secret weapon in navigating the complexities of NIS 2. The updated Network Information Systems Directive (NIS 2) expands the scope of the original NIS, impacting a wider range of organizations and introducing personal liability for non-compliance. With potential fines reaching into the millions, it’s crucial to take action […]
Experts predict a future where SOCs are not just reactive, but proactive and predictive, leveraging AI and automation to stay ahead of increasingly sophisticated threats. The Security Operations Center (SOC) is the heart of any organization’s cybersecurity posture, and its evolution is critical for MSSPs/MSPs. A key trend in this evolution is the consolidation of […]
Organizations need to bolster their defenses, and a powerful combination that deserves attention is the integration of Public Key Infrastructure (PKI) and Hardware Security Modules (HSM). In today’s digital landscape, where cyber threats evolve with alarming speed and sophistication, protecting sensitive information is paramount. Integrating Public Key Infrastructure (PKI) and Hardware Security Modules (HSM) is […]
By addressing vulnerabilities and strengthening your Microsoft 365 security posture, you can safeguard your critical data, protect your organization’s reputation, and maintain the trust of your customers and stakeholders. A recent CoreView study of 1.6 million Microsoft 365 users paints a concerning picture: a staggering 90% of organizations have misconfigurations leaving them exposed to attacks. Without the […]