Embedded cryptography integrates secure cryptographic algorithms directly into hardware or software to protect data and communications in small, resource-constrained devices. From our smartphones to our payment cards, cryptography plays a silent but crucial role in protecting our sensitive data. But what exactly is embedded cryptography, and why is it so vital? Let’s unravel the layers […]
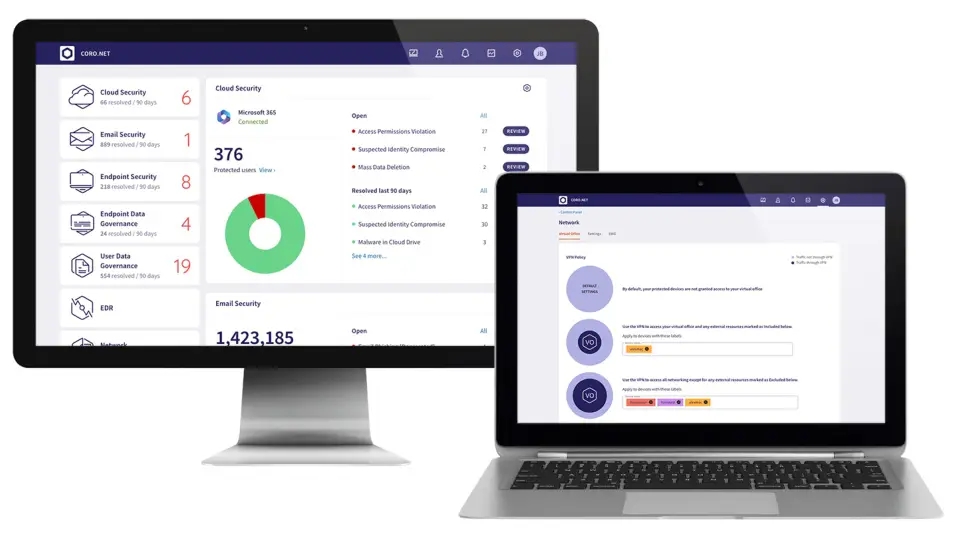
While M365 Business Premium offers enhanced security, exploring specialized cybersecurity solutions like Coro can provide significantly greater coverage and protection for your organization. Relying solely on Microsoft 365 (M365) defenses, even with E5 or E6 licensing, is a risky gamble. Many organizations mistakenly believe they’re saving money, but the reality is, it’s not a matter […]
Understanding the basics of cryptography will help you combat emerging cryptanalysis threats. The invisible shield of cryptography protects our data, from online banking to secure messaging. But what exactly is cryptography, and how does it differ from its counterpart, cryptanalysis? What is Cryptography? Imagine sending a secret message that only your intended recipient can read. That’s the […]
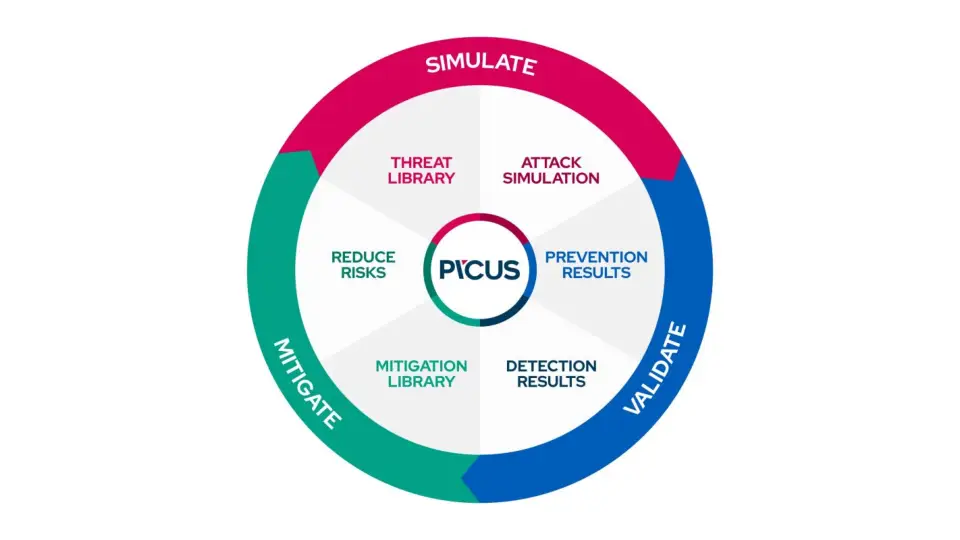
Breach and Attack Simulation (BAS) can reveal a lot more security weaknesses than your usual checks, showing you 30-50% more. However, it’s not always a smooth process. Breach and Attack Simulation (BAS) is a proactive cybersecurity approach that helps organizations test and assess their security posture by simulating real-world cyberattacks. By continuously running automated attack scenarios, BAS […]
In today’s world, where government influence and emerging technologies like quantum computing are changing the rules of digital security, taking control of our data isn’t just a technical choice—it’s essential for protecting our privacy and ensuring a safer digital future. Recent events have shown that even big tech companies like Apple are being pushed by […]
The modular revolution is more than just a trend—it represents the future of cybersecurity. By embracing this flexible approach, businesses of all sizes can maintain robust security in an ever-changing digital world. Small and medium-sized businesses (SMBs) rely heavily on technology. This increased dependence has placed cybersecurity at the forefront, fueling the demand for innovative […]
In an era where cyber threats are becoming increasingly sophisticated, safeguarding your business’s sensitive data is no longer a choice, but a necessity. Traditional software-based security measures are often not enough to protect against determined attackers. This is where Hardware Security Modules (HSMs) come in, offering a robust and virtually impenetrable layer of protection for […]
By understanding phishing tactics and embracing advanced threat monitoring, organizations can disrupt the cycle of phishing attacks, safeguarding both their brand and their customers from the ever-growing threat of cybercrime. Phishing attacks remain a leading cybersecurity threat, increasing by 34% in 2024 compared to the previous year. With 91% of cyberattacks starting from phishing emails, […]
Hardware Security Modules (HSMs) emerge as critical components of a robust security infrastructure, acting as impenetrable fortresses for your most valuable cryptographic keys and sensitive data. In an era defined by digital transformation and escalating cyber threats, protecting sensitive data is paramount. Traditional security measures, while essential, often prove inadequate against sophisticated attacks. What […]
The cybersecurity landscape is constantly evolving, and 2025 promises to be a year of unprecedented challenges and opportunities for Chief Information Security Officers (CISOs). The rise of artificial intelligence (AI), while offering immense potential, also introduces new threats and complexities. CISOs must stay ahead of the curve by understanding these emerging trends and leveraging AI-powered […]