Your Data, Your Keys: Securing Google Workspace in the EU

Google Workspace makes collaboration seamless, but without independent encryption key control, sensitive business data can still be vulnerable.
As data privacy regulations evolve, relying on default cloud security can expose organisations to compliance risks and unauthorised access. With teams collaborating digitally and sensitive information flowing through apps like Google Docs, Gmail, and Google Drive, all while compliance rules keep evolving, organisations need more than just strong passwords. They need real control of their data. That’s where crypto key management comes in. It might sound technical (and it is), but at its core, it’s about one simple thing: keeping your most important data private and protected.
Now, thanks to the integration of Utimaco’s Enterprise Secure Key Manager (ESKM) with Google Workspace’s Client-Side Encryption (CSE), businesses can combine the flexibility and productivity of Google’s cloud apps with strong data protection. At the same time, they gain the security and control of an independent, enterprise-grade key management system.
Here is how the integration works, why it matters, and how it empowers your organisation to take control of its data.
Crypto Key Management Superpowers
What is Cryptographic Key Management? It’s a system that can hold multiple superpowers, such as secure storage, reliable management, and central control across an organisation’s complete crypto key inventory.
And now its magic is needed more than ever, especially in the context of cloud-based applications. With organisations and individuals around the world sharing data, cryptographic key management ensures the highest security and privacy for the data being generated, transferred, shared, and stored.
A great example of how a superior Key Management System can provide centralised security for a variety of applications is our latest integration of ESKM with Google Workspace CSE.
Combining Productivity and Security
The integration of ESKM with Google Workspace CSE provides significant added value to organisations using Google Docs, Drive, Calendar, Meet, and Gmail. It enhances data security and protects corporate content, communications, and collaboration in the cloud.
Based on its highly secure architecture, ESKM enables the reliable and compliant storage and management of encryption keys through one central access point – cloud-agnostic, vendor independent, and highly scalable.
How the Integration of ESKM with Google Workspace CSE Works
Google’s Workspace CSE enables organisations to encrypt and decrypt their workspace data off-cloud, preventing unauthorised access while used in the cloud. Thus, Google has no access to the data because it is encrypted at the client, rather than Google servers, using a key only known and possessed by the client. Google Workspace CSE with ESKM enables data privacy, sovereignty, and maximum compliance!
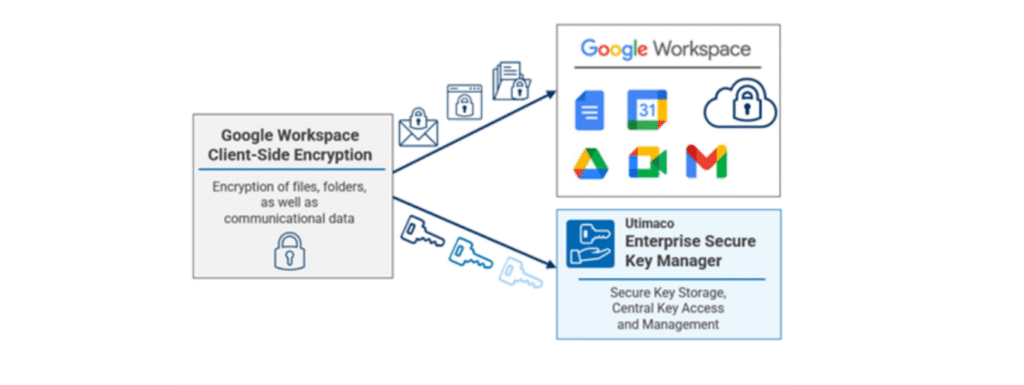
The integration with ESKM adds independent key management, control, and compliance for the usage of Google Docs, Drive, Calendar, Meet, and Gmail. It provides the single pane of glass for central key storage and management. As an external key store and access control entity, it enables organisations to maintain full control over their keys and access to content by seamlessly integrating with Google Workspace and not relying on Google’s native key management and access infrastructure.
Top Benefits of ESKM’s and Google Workspace’s integration
The integration with our flagship Key Management System provides several key benefits for Google’s Workspace CSE applications, such as:
- Enhanced Compliance and Regulatory Adherence
- Securing Sensitive Communications in Google Meet and Gmail
- Control Over Encryption Keys with Cloud-Native Scalability
- Secure Collaboration and Sharing with External Partners
- Simplified Key Lifecycle Management
- Protection of Data-at-Rest in Google Drive
- Seamless User Experience with Easy Adoption
- Improved Security for Remote Work and Hybrid Environments
- End-to-End Security for Business Continuity
The integration of Utimaco’s key management technology with the latest CSE service will help organisations migrate their legacy, enterprise work environments to Google’s secure, cloud-based collaboration services while maintaining data privacy, control & compliance!
Why Choose ESKM for Crypto Key Management?
Utimaco’s ESKM is the single pane of glass, providing central access and management of all crypto keys; independent of their origin, whether for the cloud or on-premises.
It provides full key control throughout their entire lifecycle, ensures compliance with security policies and regulatory requirements such as GDPR, NIS 2, and DORA, and helps to create reliable audit trails, helping to track who accessed what data at what point of time. This is particularly crucial for organisations operating in the EU, as both NIS 2 (Network and Information Systems Directive 2) and DORA (Digital Operational Resilience Act) place strong emphasis on robust cybersecurity measures, including effective cryptographic controls and key management. ESKM offers the independent control and auditable processes necessary to meet these stringent European regulations.
Discover Utimaco’s Key Management solutions and their flexible deployment options, either as hardware, virtual appliance or as a Service offering.
In conclusion, taking control of your encryption keys with solutions like Utimaco’s ESKM is no longer just a best practice, but a necessity for organisations navigating the complexities of modern data security and regulatory landscapes like NIS 2 and DORA. For organisations looking to implement top cryptographic solutions and ensure proper protection, CREAPLUS cybersecurity and cryptography experts can provide the proper consultation and implementation support needed to safeguard your valuable data and achieve full compliance.

